Enhancing Device Security with Secure Boot Process
Introduction:
In the realm of cybersecurity, securing the boot process of devices stands as a critical safeguard against malicious attacks. The Secure Boot Process serves as a cornerstone in fortifying system integrity and thwarting unauthorized access. In this article, we'll delve into the intricacies of the Secure Boot Process, its components, and its pivotal role in ensuring device security.
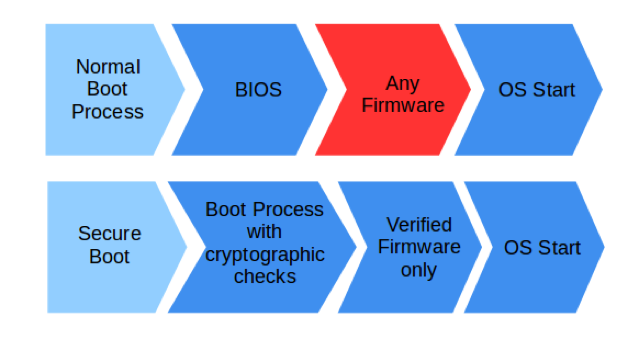
Understanding the Normal Boot Process:
Traditionally, devices follow a sequential boot process starting from power-on to the initiation of the operating system. However, this conventional approach lacks robust security features, leaving devices vulnerable to firmware replacement or spoofing attacks.
The Need for Secure Boot:
Recognizing the inherent vulnerabilities in the normal boot process, the adoption of Secure Boot becomes imperative. Secure Boot mitigates threats by incorporating cryptographic mechanisms to verify the integrity and authenticity of firmware during boot-up.
Key Components of Secure Boot:
1. Private Keys: Private keys, generated in the factory, are used to sign firmware during the manufacturing process. These keys serve as a crucial element in establishing trust between firmware and the device.
2. Signature Verification: Firmware signatures, created using private keys, are verified against stored public keys during boot-up. This process ensures that only authenticated firmware, signed with trusted keys, is permitted to run.
3. Hashing Algorithm: Hashing algorithms like SHA-1 compute unique hash digests for firmware. These hashes are compared during signature verification to detect any modifications or tampering attempts.
Primary and Secondary Boot Loader:
The Secure Boot Process employs a Primary Boot Loader (PBL) responsible for initializing the boot sequence. Additionally, a Secondary Bootloader (SBL) verifies firmware signatures, writes firmware to flash memory, and ensures secure boot continuation.
Examples and Illustrations:
In a trusted execution environment, such as a trust zone, secure boot components execute within a secure context. Trusted execution prevents attackers from tampering with critical security firmware, ensuring the integrity of the boot process.
Performance Impact Analysis:
Despite its cryptographic overhead, the performance impact of Secure Boot remains minimal. With the addition of an RSA public key and SHA-1 hashing algorithm, the boot process incurs a negligible delay of 30 milliseconds or less. This marginal impact is justifiable, considering the significant security enhancements it provides.
Conclusion:
In an era characterized by escalating cyber threats, the Secure Boot Process emerges as a vital defense mechanism against malicious attacks. By leveraging cryptographic techniques and trusted boot components, organizations can fortify device security, safeguarding against firmware tampering and unauthorized access. As technology advances, ensuring the integrity of the boot process remains paramount in preserving device integrity and protecting against evolving threats.

Comments
Post a Comment